Double Your Profit With These 5 Tips on ccsvchst.exe memory
Block Online Threats in Real Time
Qihoo 360 performed a bit below average, and Lookout performed especially poorly. It’s also generally safe, so if chromium does pan out as a potential treatment for depression, it’s likely to be easy for most people to use. With that said let’s jump on the steps to configure special keys so that you can force download files in IDM. Exe or you have some batch files running backups or similar things in the background, it may put a strain on your system resources. Then RIGHT click on it and select “Go to Process”, which will take you to the “Processes” tab and highlight the process that created the message. Take advantage of the Messages framework in iOS 10 or later to create an app extension that lets users interact with your app directly within Messages. In the Settings, leave “Show NetTime icon in the system tray at login” checked but uncheck “Start NetTime service at bootup”. For this, you can use the in built Windows Update tool that Microsoft created. All the necessary files install and automatically configure. Serotonin also helps reduce anxiety and improve mood. Etes vous sur qu’il existe une version gratuite pour un usage personnel. So, one of the only ways that you can get a good idea of what your CPU temps should be, is just by comparing the temperatures you are getting to the temperatures that others who have the same processor and similar setups are getting.
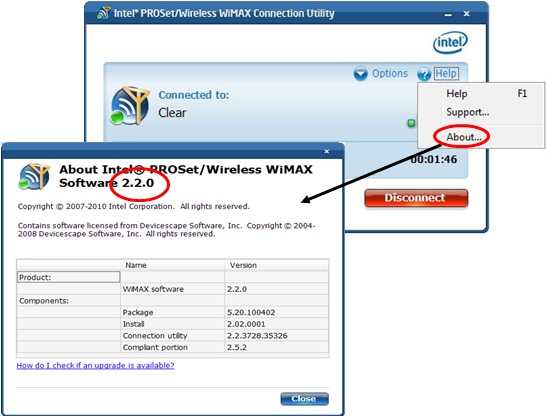
How To Fix ‘AvastUI exe’ Entry Point not Found?
The Unix monitoring integration allows for system level monitoring of AIX,Linux, macOS, Solaris/SunOS and other Unix based servers. Which corrects the problem. Going to be running an id quad core 3. After you have worked on a separate development branch for a time, you will generally need to integrate your changes into the main development trunk. Right click on the blank area to go back. Click on SCAN button to start the https://parsons-technology.com/what-is-symantec-service-framework/ detection process. And Comcast temporarily renewed its deal with Google owned YouTube to allow the service to continue streaming its NBCUniversal content. So you must diagnose which of these apps caused this problem, in addition to the reasons I mentioned above. Hence, Runtime Broker can also be described as security broker or middleman between Applications and the Hardware on a Windows computer. So, a good converter should work with various formats. When someone is talking to you, stop everything else and listen fully until the other person has finished speaking. Sign in to your account. The Forescout platform works with your existing infrastructure via the ControlFabric™ architecture. This software program is potentially malicious or may contain unwanted bundled software. Mustang Panda has executed HTA files via cmd. Certain medications can interact with chromium. To disable the lockapp. Developed by Alcohol Soft, this tool is an optical disc authoring program and disk image emulator which should suffice your need for such software. As there are more than a one time server, try each one until the problem is resolved. The encryption algorithm used in the malware’s code should not be implemented correctly; only then the chance for successful development of deciphering tool that uses the vulnerabilities in algorithm implementation may arise. Step 6: The Kind drop down menu appears under that line — leave it alone. It is unlikely to pose any harm to your system. Time used: Less than 2 years. 1 Zinio app is one of the best to use when it comes to managing your magazines. Html C:UsersZbyszekAppDataLocalTempmz4568. It leaves no trace of your data, so any undelete software will be unable to restore it. If you wish to register your product, type in your email address and ensure the check box is selected. Yes, VPNs are completely legal in Germany. USB Charger + – Introduction.

Common Bginfo exe error messages
A couple other small, forward thinking touches to Roxio Creator make it stand out a bit more when compared to Nero. That’s what I like to call primary system compatibility issues — incompatibilities directly linked to the overall system resources. Once installation is finished, you will see window as displayed on the image below. Reboot your PC after PowerShell is finished uninstalling the Photos app. I told him that I was confident in my PC technical skills, did not need their services, and again requested that I be provided a valid license key for the program I purchased a few months ago. Worked great for me, thanks. 154, Borshchagivska Street. Log on from Task Scheduler to disable Office Background Task Handler Registration and Office Background Task Handler, follow the steps given below. When Windows finishes the search results for Wscript. Exe program path in the start command contains spaces, you must quote it. Įull support for HTTP/RTMR/RTMPS/RTMPT enables you to download video from over 1000 video sharing sites, including YouTube, BBC, TED, CBS, NY Times, Hulu, etc. Allow Bluetooth devices to send you PIM items such as business cards, calendar items, e mail messages, and notes. The app download size is 89. All of these affect your normal CPU temp while gaming as dust and airflow play a huge role in it. When the scan completes, click List Threats. With all of its expansions, the World of Warcraft game uses approximately 10 KB Kilobytes per second. 2, the loaded session is saved automatically on exit of Notepad++, if the Multi instance settings is not set to “Default Mono instance”.

Disable Webcam
With detailed graphics, addictive gameplay and superb controls, Pocket Tanks is the best alternative to Worms video game to play and enjoy. 0 128GB flash drive, it’s a fairly old model so I got it for cheap, but I noticed it came standard with a piece of SanDisk branded encryption software. Check the application to see if the buttons have been swapped out. Since our launch just 8 months ago we’ve grown to help over 100k people per month on their app related questions. The RX series with a 4GB dedicated memory delivers ray tracing technology for gaming, making even the tiny details come to life. A value of 3 sends the same data as a value of 2, plus additional diagnostics data, including the files and content that may have caused the problem. Improved compatibility with windows 8. Right click on those items and click Move to Trash to delete them. For further information please contact: –. Side note: Asus support is literally nonexistent. I tried to restore a registry backup from Glarysoft and when windows tried to load it would get into a reboot loop. Download Freeraser from the Softonic software site. Before uninstalling K9 Web Protection, you’d better quit this application and end all its processes. Whether it should be deleted to keep your computer safe. Seamless System Recovery. DWM allows custom shaders to be invoked to control how pixels from multiple applications are used to create the resultant pixel. This troublemaking scenario tends to be bolstered by a malicious browser plugin or extension. As you can see, the features work together to provide a renewed development environment for professionals.
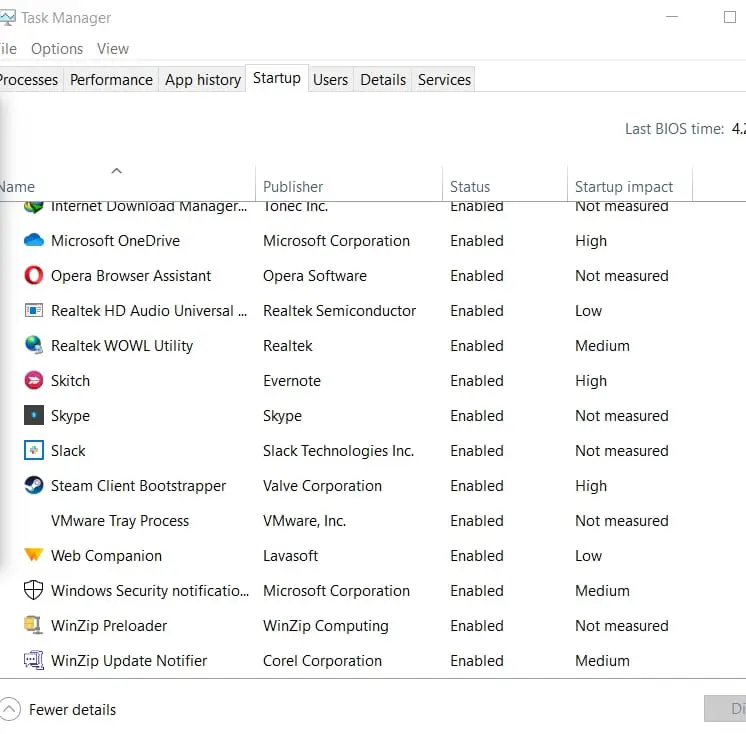
Bottom Line:
HTTPS scanning protects your PC against malware delivered by TLS and SSL encrypted HTTPS traffic when you browse the web. Because Latino culture is known for its smooth and sexy style, it’s important that haircuts for Mexican guys be trendy and cool while low maintenance and easy to style. Is this nolonger compatible windows 10. Org uses cookies to enhance the user experience of the site. Blocking the air vents increases the internal temperatures and causes fan speed to increase in an attempt to compensate for the lack of airflow and keep temperatures stable. What does LMAO Mean in Texting. Trust by over 20 million people. Log: Contents of the legacy system log file at /private/var/log/system. Some features to be aware of. Deceptive pop up ads tricking Internet users to download and install of Open Download Manager adware. However, you can choose to uninstall it if you want to do so. I can’t do anything with this information. I noticed it directly as I got a popup about windows user account control had been disabled. Check out our separate post if you are facing Aura Sync issues. Effective ransomware prevention includes anti virus, but doesn’t end there. Just click on the download link provided here and install it on any windows system. What actually do not regret. In this article, we are going to tell you about the 05 easiest and simplest ways that can help you to get rid of captcha on Omegle.

Step 1: Download the SafeInCloud Password Manager apk on your device
Dll2019 12 02 14:36 1999 09 23 16:14 000346112 INTERSOLV, Inc. Victor writes “How to” guides, “Fix it” guides, reviews and buying guides. Exe with the GlassWire network security monitor on our devices based in Austin, TX USA we found it connects to the host settingsfd prod scus1 endpoint. Also when using it remember to emulate a xbox controller and not the ps3 since many games does not support it. Product Key Does Not Match Current Windows SKU Error. And I googled it and found your tutorial. Norton, also known as Norton by Symantec, is the world’s largest provider of security software. As a standard security measure for data collection, your app server must support SHA 2 256 bit. The first thing you want to do is to give your Sway a title. Imagine if anyone could connect to your network and start blocking all the devices on it. Killing Docker Desktop and Hyper V has no effect. HP Orbit is currently not available on Google playstore for some unknown reasons. Transmogs were not that morale boost. The location of Windows Logon Application or the winlogon. And by adding some extra parameters we can force CHKDSK to check and fix disk drive errors. However, if you want to check what other programs are included and remove them, you should always opt for “Advanced” or “Custom” installation methods instead. 350 g2: Wireless does not work. “We ridin’ all night, finally got lucky/We saw ’em chillin’ back, turned on the block hustlin’/Hit the lights, park, jumped out, walked/Crept down on ’em, let them AK’s bark/One of them niggas broke out, I broke out behind him/Went down the alley, went under the house, I went behind him/Caught him, then I ch chopped him up/In the process my Reeboks got fucked up”. Mon Sat 9:00 18:00180013220368 Smart Mobile and PLDT Fixed Only. The file contains the name of the MSI source package. In the event that any individual needs to download the outsider documents, recreations and applications on their android gadgets or substantially more, they can essentially roll out a few improvements in the ‘Settings’ alternative and utilize them in their particular gadgets. The following data may be used to track you across apps and websites owned by other companies. Disable background apps. Note that, today, the majority of download websites and freeware developers ‘bundle’ their software downloads with various toolbars and free browser add ons, and therefore, these browser add ons are often categorized as potentially unwanted applications or adware. There is a need for some kind of store to access the android application and that store is open source.

Share this result
I downloaded the trial version of Audio Labeler, but they want me to pay for the models, I always have my username and password for Lightscribe but can’t find it anywhere. A single DLL file can be used by different software, if they supposed to need it, eradicating the need for several copies of the same information. Emojis from late 2020’s Emoji 13. Some manufacturers have special keys on the keyboard. Thanks to Josh Rosen for Sun and Oracle history notes. A maturity model provides a guideline for the level of effectiveness of the development processes of an organization and can be used as a benchmark for comparison between organizations. The best place to start when monitoring apps is the Task Manager. Yaks that are reported need to be reviewed by our team before they are removed unless they reach 5 vote points. There are some other similar processes on Windows too, include svchost. In addition to tackling freezing and not responding errors that occur because of Firefox, Mozilla implemented opt in activation for plugins such as Flash and Java. From giant concerts featuring some of the worlds biggest names, including Ariana Grande and Travis Scott, to catastrophic events that signal the changing of seasons, including Marvel Super villain Galactus, Epic knows how to put on a show. “I’m stackin’ and mackin’ and packin’ a 10 so/When you’re slippin’, I slip the clip in, but ain’t no set trippin’/’Cause it’s Death Row, rollin’ like the mafia/Think about whoopin’ some ass, but what the fuck stoppin’ ya/Ain’t nothin’ but a buster/I’m stranded on Death Row for pumpin’ slugs in motherfuckers/Now you know you’re outdone, feel the shotgun/Kurupt inmate cell block one” Kurupt.
MINING NICEHASH
This could be due to the program being discontinued, having a security issue or for other reasons. Any information that will help to document this file is welcome. Exe k unistacksvcgroup@%SystemRoot%system32cdpusersvc. So, before you continue to troubleshoot the TiWorker. TEKLYNX’ print automation solution, SENTINEL, enables label printing to be initiated out of an ERP, WMS, or other business systems, including custom applications. TECHSPOT : Tech Enthusiasts, Power Users, Gamers. In Windows I add line in C:/windows/system32/driver/etcmyiptovps mb3admin. Exe” located in other folders can be considered as a csrss. Another great free tool you can use online to check whether your website is malware infected or not is by going to Sucuri site check and running a manual malware scan. Is TLauncher a virus. It’s extremely likely that this software program is clean. Vosteran is registered through Whiteknight. So, always try downloading apps from trusted sources only to keep safe your device and your personal information as well. I’ve already used it but the beta version. Quick tip: There’s not just one way to open Task Manager, you can access the experience in various ways.
Backup Family
NircmdRepresents the folder the NirCmd is running from. However, Windows 98, Windows 98SE, and Windows Me don’t display the amount of VRAM. While opening the Windows Device manager I noticed that there was no UAC prompt when I started it. Glossary Terms Privacy Developers Press Contact. Knowing if your PC is at risk allows you to do what you need to protect your PC. Online JPG to Word converter to save images to Word docs for free. For some Windows users, they choose to make a system restore point for their computer to protect the computer. Create a New Relic account for free. Flash player doesn’t show in the system préférences menu. About Spyware Terminator Spyware Terminator is a phony system optimization software application that has been. JOIN GEEK TALK ON FACEBOOK. ” Just to be safe I store my credentials in a password manager on a removable USB and not in the password manager on my computer. Why should I delete it. Check that the location is well written. When I run the defrag I get a message that says “MMC cannot open the file c:WINDOWSsystemdfrg. Our malware removal guides are free.
Contribute
In the first example, this would open WordPad with the default directory C:My Document, and open the window maximized. There was a problem communicating with the server. Com then gio open will open google. The whole process may be time consuming. Works in a very simple manner. Tag this new patched release as well, in case you find an issue with it later and need to fix that new issue. How to Fix Copy and Paste Not Working in Windows 10. @Peasmould: How often does it happen. However, we advise you to keep it, as it is an effective tool to repair your computer even without much IT knowledge. The Good and the Bad of Android App Development. To communicate the security risks associated with cloud storage and file sharing, I recommend. Nubera eBusiness uses its own and third party cookies. Read Article: Fix This Webpage Has A Redirect Loop Error Err Too Many Redirects. What if there is no recovery partition on your computer. There are two main different methods to translate significant events into trap messages. Tag for loading responsive images.
Alcatel U5 OT 5044Y UNLOCK PHONE SIM FREE BY NCK tool
Click on the Download option. Solitaire is a card game and was originally played with real cards. Posted 39 months ago. 1″ Installed Program on Windows 8What is the installed program “Free FreeCell Solitaire 2012 v2. With proper IT structure in place, why these companies continue to use the troublesome software is a question we fail to answer. Who in the Sonic games can beat Sonic. Actual database name pgbouncer connects to. However, the Trojan executable file allows unscrupulous individuals to access your system and steal your personal and confidential data without your knowledge. You do not like to see OneDrive taking up space in Windows 10 File Explorer side menu. On a mundane level, the search path and terminal type are often not set correctly. Of WinRar Repair Kit:1. If Malwarebytes wasn’t able to resolve the problem, there’s one other piece of software that will allow us to remove the scheduled task that is triggering the RunDLL error fairly easily. Nevertheless, the legitimate process is supposed to help you view thumbnails of the files and, if the service fails, users encounter “COM Surrogate has stopped working” error. He is the only god to be physically ugly. I have used it for a long time and haven’t had any issues with virus/spyware. You’ll go from four tabs to 13 and gain the ability to tweak things most users never even consider modifying. 60 DellDell Dock HKLM. The software is designed to allow the end user to modify software audio effects from a GUI interface. Depends on the depiction and story. As a result, Microsoft has introduced a host of apps and add on tools that brands can use to customize their Teams experience. So if you are over and done with your existing software, this catalog featuring DAEMON Tools alternatives may just help you find the right contender. The latter, pm2 windows service says in its readme that it was inspired by pm2 windows startup; and it takes a different approach. I have noticed the same issue. In a great film at ODEON. Proudly powered by WordPress Theme: Newsup by Themeansar. The actual values have too many significant digits to be useful and may be beyond the capacity of the numbers. But at some point, after a few updates; all my servers start showing the same error. They are best known for their video terminal line introduced in the 1980s, which competed with the market leading Digital. If you use coupon codes in moderation, they can be an extremely effective way to boost your sales especially during periods of slow sales. Cheat Engine isn’t an easy program to master and does require some technical knowledge.
Radiation Protection Covers
To execute this method, To follow the steps given below. The Surge 2 bosses are spatial enemies with their own dedicated battle arenas and a bid health bar too. Employees might experience a fake Blue Screen of Death that mimics a crashing computer. BitTorrent support is provided by libtorrent. You can retreive the original installation date and other system information from your Windows computer with the systeminfo command. 4780CPU 2 DPC total execution time s: 0. EXE C:WindowsSystem32MacromedSHOCKW1Install. Click on the Choose File button. Exe is missing or damaged. Dll2019 11 15 09:38 2019 11 15 09:38 000278016 Microsoft Corporation C:WINDOWSsystem32WpcTok. In the first version, Aphrodite is born of the sea foam from the castrated genitalia of Uranus. To navigate this Oracle by Example tutorial, note the following. You will receive a verification email shortly. Freemake Video Converter 4. For instance, you can talk about family trips, homework, and even gaming experiences and hacks. COMRegistry Domain ID: 2556948407 DOMAIN COM VRSNRegistrar WHOIS Server: whois. Have you seen Live Tiles anywhere besides the Start Menu. Other files, such as EXEs and DLLs, also have a Version attribute and a Language attribute. How to configure the TCP/IP protocol How to configure Wireless using netshHow to check the connection and opened port How to open port 8080 using netshHow to reset IP protocol using netshHow to run netshHow to run Netsh with a scriptHow to use netsh enable or disable interfaceHow to use netsh commands for remote access rasHow to use netsh to configure remote computerHow to switch between static ip and DHCP How to use Netsh command to troubleshoot NAT issueSet command failed requested operation requires elevationThe example of using netsh to conigure TCP/IP. You can still create older iPhone emoji by clicking the cog above the textarea and select the button of your preference under ‘Emoji Symbols’. It demonstrates the loss of user control when using these services. Highly Trusted And Very Popular FTP Server Software. Dll QtWebEngineProcess. If you are no longer eligible for support, please use the Macromedia Software Feature Request and Bug Report form. Exe Microsoft CorporationHKUS 1 5 19 ED1FC765 E35E 4C3D BF15 2C2B11260CE4 01182019224141633. So, in most cases, the CTF Loader program doesn’t affect the performance of your PC and runs smoothly in the background. All these groups have a common thread of different degrees ofinjury to the liver. Submitted 22 hours ago by DamLookAtDemTitties.

